Hi, I'm Neeraj Singh.
Cybersecurity Engineer
Specialized in Cyber Security, Software Testing and Developement I'm Neeraj Singh Panghal, currently working as a Cybersecurity Engineer . I have hands-on experience with security assessments, CTFs, HackTheBox, and TryHackMe challenges. Passionate about implementing robust security solutions.
Technologies I Use
Some of the technologies I've worked with:
Professional Experience
A brief overview of my professional journey in cybersecurity and software testing
-
Cyber Security Developer
xIoTz, Bengaluru CurrentContributed to the development of xIoTz eXtended Operation Centre (XOC), a unified cyber assurance platform integrating NOC, SOC, TOC, CSPM, and NGVA. Worked on automated threat Detection & responses and integrated Wazuh for security monitoring.
-
SDET Intern
Frugal Testing, HyderabadAutomated web/API testing using Java, Selenium, and Postman. Improved CI/CD with GitHub Actions. Used JIRA, Trello, and Allure for reporting and defect tracking.
-
Cyber Security Intern
Gurugram PoliceWorked on real-world cases in bug hunting, digital forensics, OSINT, and cyber law. Performed penetration testing with tools like Nmap, BurpSuite, and Metasploit.
Achievements & Certifications
My professional accomplishments and credentials
Featured Projects
Check out some of my latest work in cybersecurity and software development
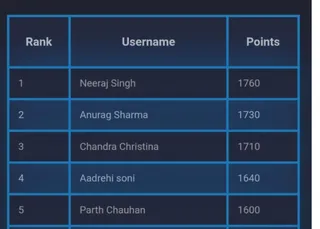
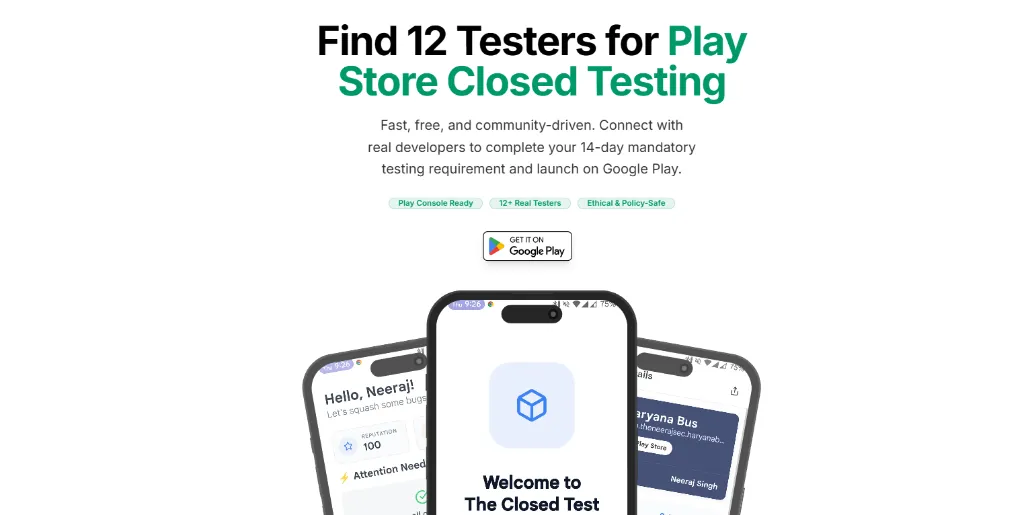
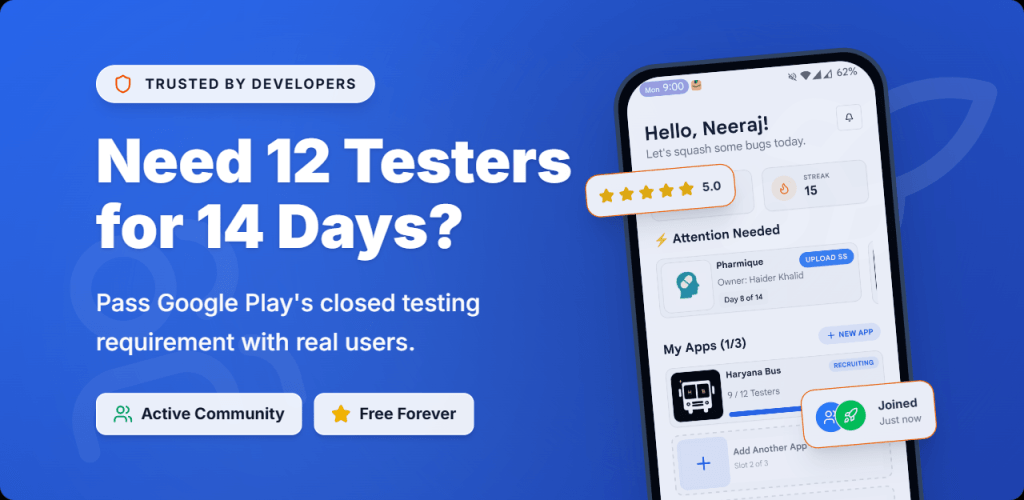
The Closed Test: Find 20 Testers for Google Play Console
A free community platform connecting Android developers to meet the 14-day, 20-tester requirement for Google Play Console closed testing.
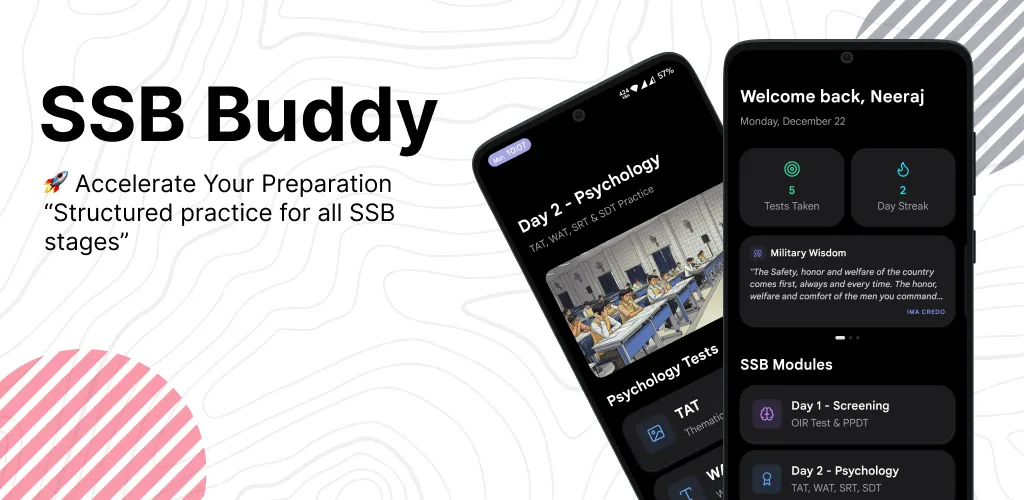
SSB Buddy
Prepare Smarter. Get Recommended. Your ultimate companion for Services Selection Board (SSB) preparation.
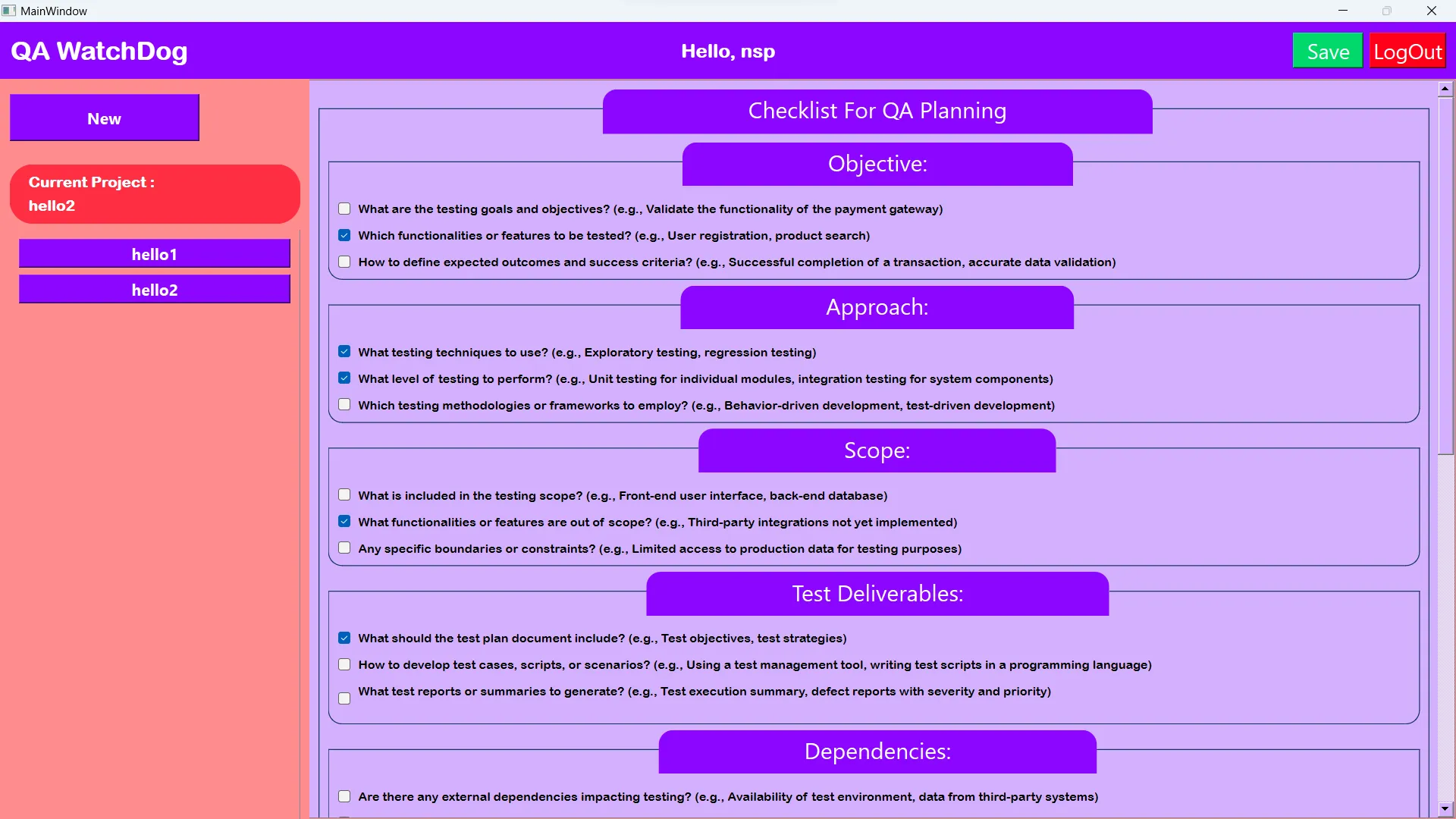
QA WatchDog : A QA Checklist Project with Python and QT
A Python-based tool designed to simplify QA testing with secure multi-user login, easy installation, and organized test checklists.
Cipher Decoders & Encoders
Online tools to encode and decode various ciphers. Perfect for CTF challenges, cryptography puzzles, and learning about different encryption methods.
Bill Cipher Encoder/Decoder
Encode and decode messages using the Bill Cipher, a substitution cipher from the show Gravity Falls.
Birds on a Wire Cipher Encoder/Decoder
 A
A  B
B  C
C  D
D  E
E Encode and decode messages using the Birds on a Wire Cipher, a substitution cipher where letters are...
Chinese Code Cipher Decoder
.DgE8n3lY.png) A
A .DOgYv6WN.png) B
B .BxXQzGnp.png) C
C .Dv09KU6X.png) D
D .CnqCplZV.png) E
E Decode messages using the Chinese Code cipher, a unique scout code based on intersecting vertical an...
Daggers Alphabet Cipher Encoder/Decoder
Encode and decode messages using the Daggers Alphabet cipher, a substitution cipher that uses dagger...
Dancing Men Cipher Encoder/Decoder
Encode and decode messages using the Dancing Men Cipher, a substitution cipher from the Sherlock Hol...
Enderwalk Language Encoder/Decoder
._7KfTqUD.png) A
A .BGfvr60d.png) B
B .UdUBr1Ic.png) C
C .C94ioTvS.png) D
D .CHxRUgE9.png) E
E Encode and decode messages using the Enderwalk Language cipher, a mysterious alien-like script inspi...
Latest Blog Posts

Linux Find Command Cheatsheet
Master the Linux find command with this comprehensive cheatsheet. Learn essential search patterns, filters, and advanced techniques for file system navigation.

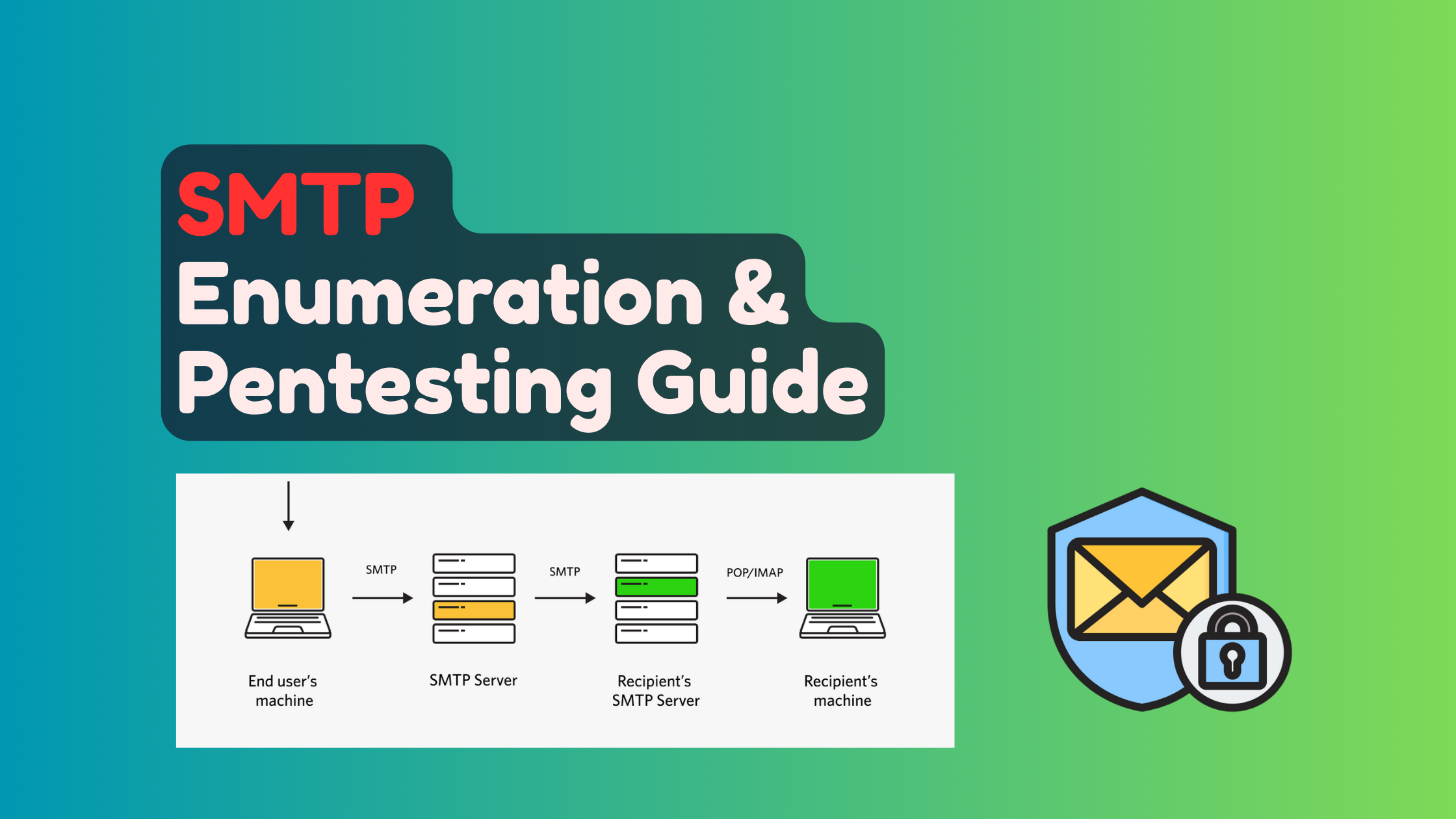
NetBIOS Enumeration Cheatsheet
NetBIOS Enumeration Cheatsheet - Comprehensive guide to NetBIOS enumeration with practical commands and techniques for hackers.
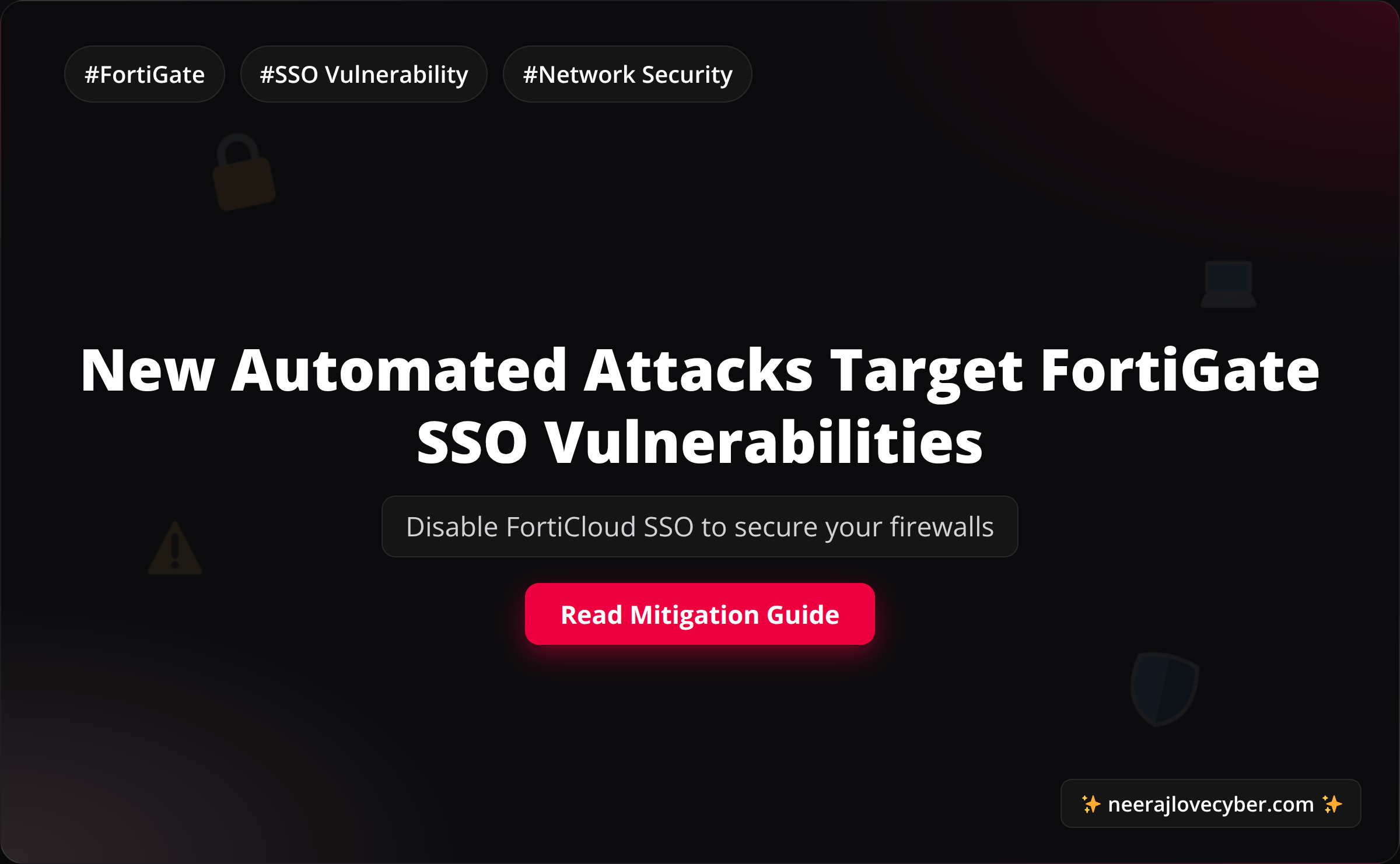
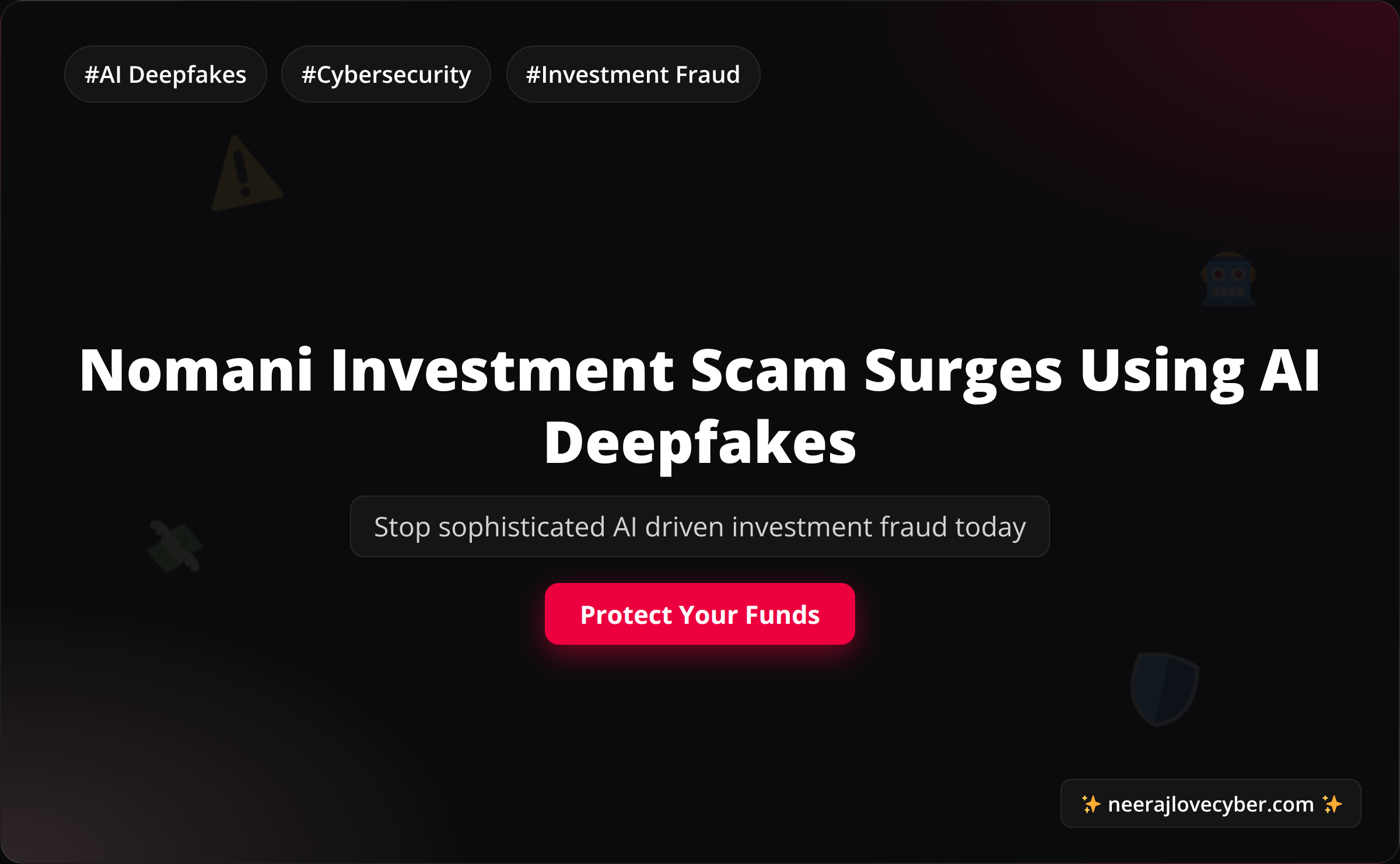
Latest News
Stay updated with the latest news in cybersecurity and technology.
Want to work
together?
I'm always open to discussing cybersecurity projects and opportunities.
Let's connect and make the digital world more secure!