Essential Nmap Commands for CEH, HTB, and TryHackMe
A comprehensive guide to Nmap commands commonly used in ethical hacking, HackTheBox, and TryHackMe challenges. From basic scans to advanced techniques.
Specialized in Cyber Security, Software Testing and Developement I'm Neeraj Singh Panghal, currently working as a Cybersecurity Engineer . I have hands-on experience with security assessments, CTFs, HackTheBox, and TryHackMe challenges. Passionate about implementing robust security solutions.
Some of the technologies I've worked with:
A brief overview of my professional journey in cybersecurity and software testing
Contributed to the development of xIoTz eXtended Operation Centre (XOC), a unified cyber assurance platform integrating NOC, SOC, TOC, CSPM, and NGVA. Worked on automated threat Detection & responses and integrated Wazuh for security monitoring.
Automated web/API testing using Java, Selenium, and Postman. Improved CI/CD with GitHub Actions. Used JIRA, Trello, and Allure for reporting and defect tracking.
Worked on real-world cases in bug hunting, digital forensics, OSINT, and cyber law. Performed penetration testing with tools like Nmap, BurpSuite, and Metasploit.
My professional accomplishments and credentials
Check out some of my latest work in cybersecurity and software development
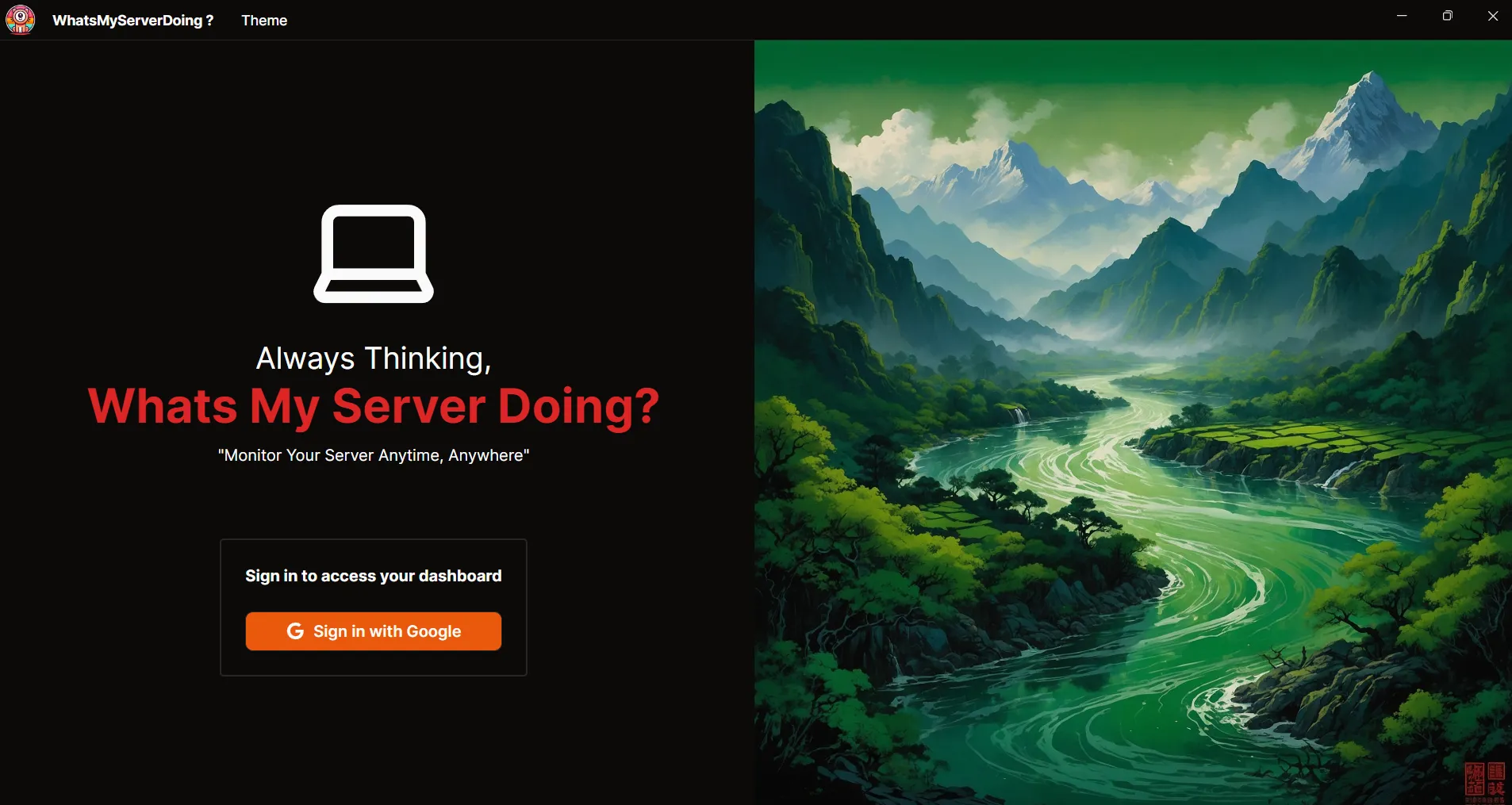
A cross-platform server monitoring tool built with Tauri and Go, enabling real-time monitoring of multiple server resources through an elegant interface.
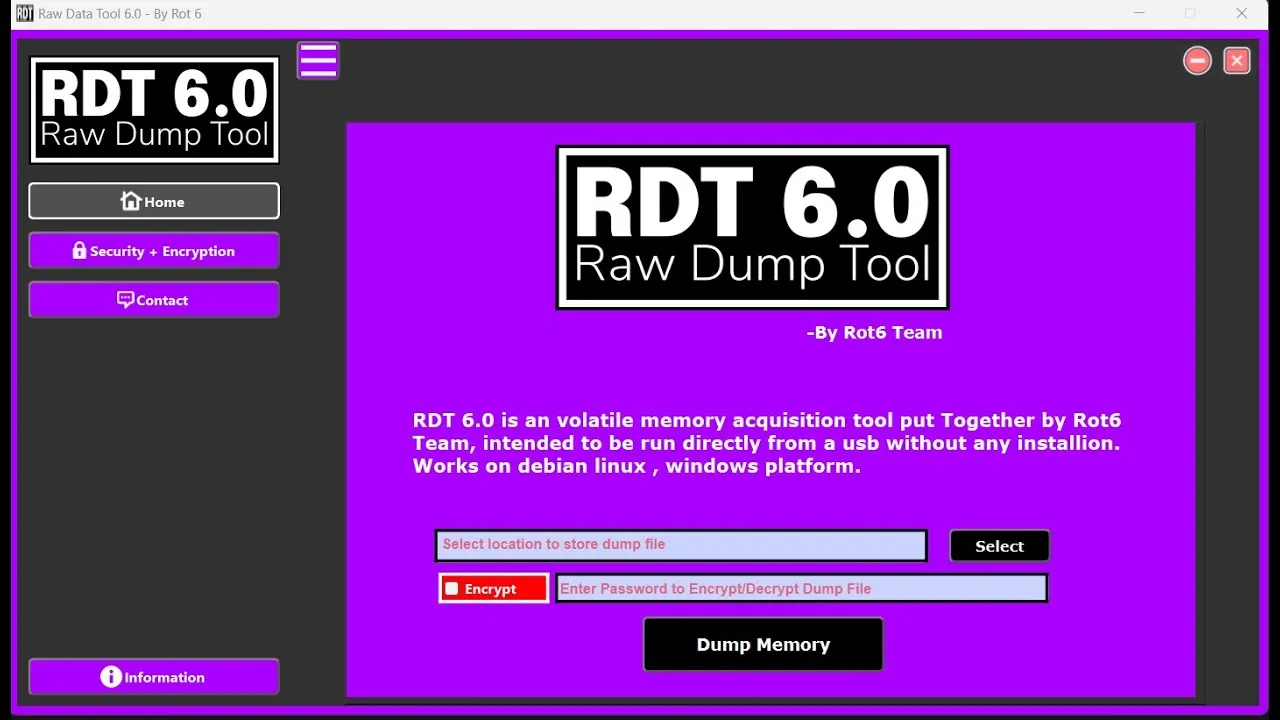
A Python-based GUI Memory Dumping Forensics Tool for digital investigators, featuring encryption, tamper detection, and comprehensive analysis capabilities.
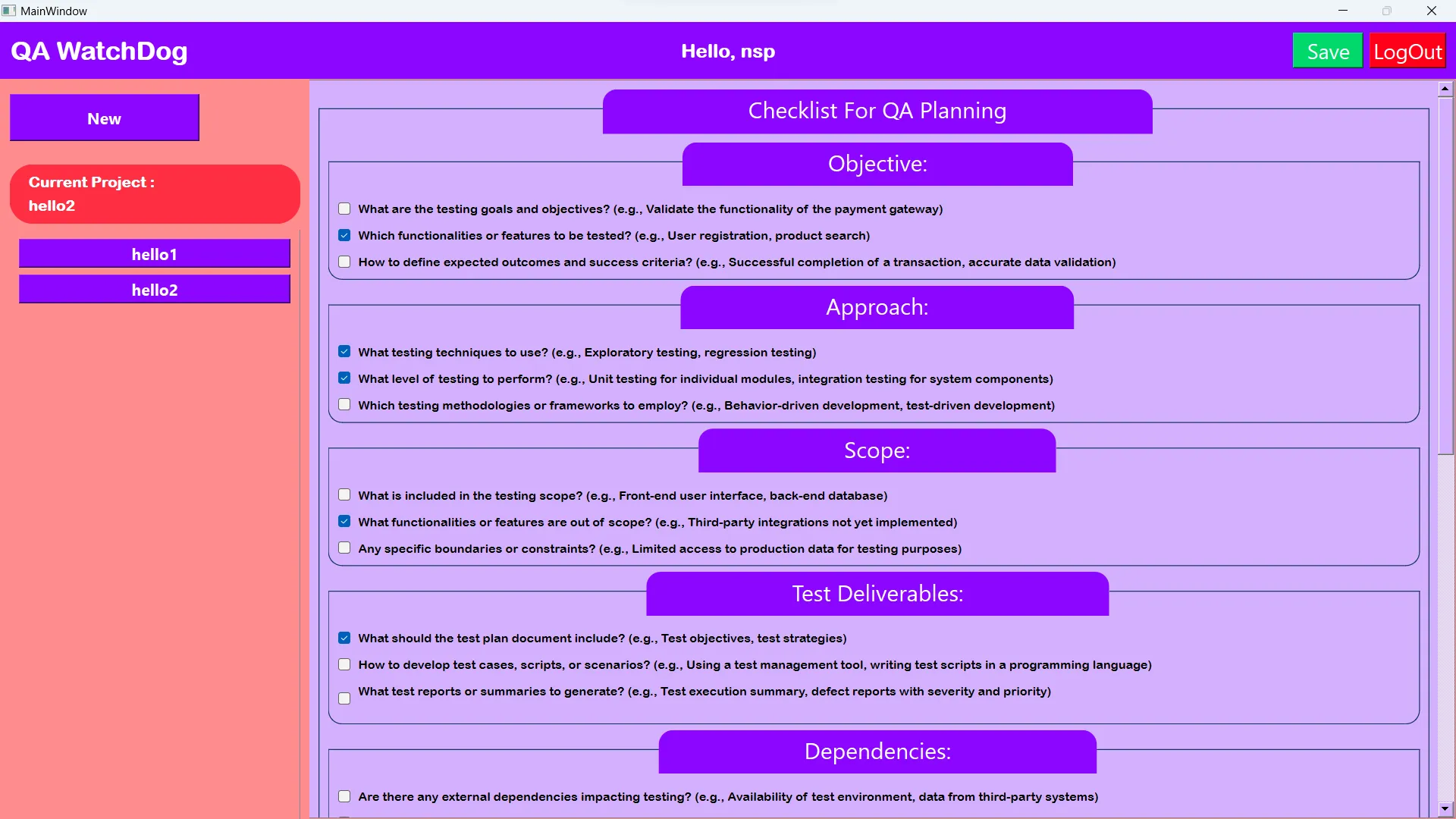
QA WatchDog is a Python-based tool created by Neeraj Singh, designed to streamline and simplify the QA testing process.
A comprehensive guide to Nmap commands commonly used in ethical hacking, HackTheBox, and TryHackMe challenges. From basic scans to advanced techniques.
Comprehensive guide to NetBIOS enumeration with practical commands and techniques for network security professionals and ethical hackers.
I'm always open to discussing cybersecurity projects and opportunities.
Let's connect and make the digital world more secure!