· Cryptography · 10 min read
CTF Cryptography Cheatsheet/Checklist

Table of Contents
12CTF Cryptography Cheatsheet/Checklist
In CTF (Capture The Flag) competitions, cryptography challenges are all about testing your skills in cracking codes and uncovering hidden messages. Think of it like being a digital detective! You’ll need to figure out how different encryption methods work, then find ways to break them. These challenges often involve:
- Old-School Ciphers: You might encounter messages encrypted with classic methods like the Caesar cipher (shifting letters), Vigenère (using a keyword), or simple substitution (swapping letters).
- Modern Crypto Puzzles: Sometimes, you’ll face more complex, real-world encryption like RSA or AES. Your task might be to find flaws in how they’re used or implemented.
- Decoding and Hashing: You’ll learn to recognize and decode various data formats (like Base64 or Hex) and understand how hashing works.
- Hidden Messages (Steganography): Cryptography often goes hand-in-hand with steganography, where messages are hidden inside other files, like images.
- Code-Breaking (Cryptanalysis): This is where you apply smart techniques to break encryption, often using a bit of math and special tools. To do well in CTF crypto challenges, you’ll want to understand the basic ideas behind cryptography, get hands-on with some common tools, and always keep an eye out for clues – sometimes, the smallest detail can lead you to the solution! Common CTF Cipher Formats & Encodings checklist (CTF cryptography Cheatsheet)
Base Encodings
Base encodings are methods for representing binary data in ASCII string format. They are commonly used in CTFs to encode flags or data, making them appear as harmless text. Common types include Base64, Base32, and Base85, each with unique character sets and padding rules.
- Base64 - Alphanumeric with ”+” and ”/”, may end with ”=”
dGhpc2lzYmFzZTY0Y2lwaGVyCg==- Base32 - UPPERCASE alphanumeric, may end with ”=”
ORUGS43JONRGC43FGMZGG2LQNBSXE===- Base85 - Gibberish-like, uses extended ASCII characters
<+oueBld\lF(I<gASu!rA8,po/lH7tASkmfE\9XoChIHk@V'RoF(b`ROT Ciphers
ROT ciphers are simple substitution ciphers that rotate characters by a fixed number of positions in the alphabet or ASCII table. They are often used in CTFs for basic obfuscation. Examples include ROT13 (letters shifted by 13) and ROT47 (all printable ASCII characters shifted by 47).
- ROT13 / ROT-n - Uses a Caesar shift within the 26 letters of the alphabet
- ROT47 - Extends ROT to 94 printable ASCII characters
- Example: “E9:D:DC@Ecf4:A96C”
Classical Ciphers
Classical ciphers are traditional encryption methods used before modern cryptography. They include techniques like Vigenère, substitution, and transposition ciphers. These are frequently encountered in CTFs and can often be broken with frequency analysis or brute force.
- Vigenère Cipher - Encrypts text using a repeating keyword (Example: “elmltwzbrrikpgmisivptxldpcpxpx” with key “leet”). Can be bruteforced if key is unknown
- Substitution Cipher - Each letter is replaced with another fixed letter
- Transposition Cipher - Rearranges the letters of the plaintext
Symbol-Based Encodings
Symbol-based encodings use visual symbols or patterns to represent information. Morse code and Tap code are common examples, translating text into dots, dashes, or taps. These encodings are popular in CTFs for hiding messages in plain sight.
- Morse Code - Dots and dashes (or “dit-dah”)
.... .. ... .. ... -- --- .-. ... . -.-. --- -.. .- Tap Code - Similar to Polybius, based on tapping patterns
.... .... .. ... .. .... .... ... .. .... .... ... .... .... . . .... . . ... ... ..... . .... . .....Biological-Looking Encoding
Biological-looking encodings mimic biological sequences, such as DNA, to encode information. In CTFs, DNA encoding uses the letters A, T, G, and C to represent data, often requiring custom scripts or tools to decode.
- DNA Encoding - Uses A, T, G, C base characters
GAGTTGAAAATATTGCGGCCGCTGGTAATGATAACATTGCGGCATTTG CTACACCGAGGCGTCGGAOther Ciphers
This section covers miscellaneous ciphers that don’t fit into other categories, such as Keyboard Shift, Polybius Square, Rail Fence, and Bacon Cipher. These ciphers use unique patterns or grids to transform plaintext and are common in CTF puzzles.
- Keyboard Shift - Based on physically shifting keyboard characters (QWERTY mappings)
- Polybius Square - Uses a 5x5 grid to represent letters by coordinates
- Rail Fence Cipher - Zigzag pattern across multiple rows
- Bacon Cipher - Binary-style A/B pattern representing letters
BAABAAABBBABAAABAAABABAAABAAABAAAABAAAAAAAABA ABBABABBAAAAABAABAAAABBBAAABBBAABAABAAAAEsoteric Languages
Esoteric languages are unconventional programming or encoding languages designed to be difficult to read, write, or understand. In CTFs, they are often used to obfuscate code or hide messages, requiring creative decoding and problem-solving skills. Examples include Brainfuck, JSFuck, Malbolge, Whitespace, and PikaLang, each with unique syntax and encoding logic.
- Brainfuck - Uses a minimal set of characters like ”+”, ”-”, ”>”, ”<”, ”[”, ”]”, ”.”, ”,”. Each command manipulates a memory array.
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++++++++++. ------------.+.++++++++++.----------.++++++++++. -----------------.++++++++++++++++.-----------------. ++++++++.+++++.--------.+++++++++++++++. ------------------.++++++++.- JSFuck - JavaScript written using only 6 characters: ”!+”. Used for obfuscation or in CTF challenges.
[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])...- Malbolge - Infamously hard to write and understand. Produces gibberish-looking text (similar to Base85).
('&%:9]!~}|z2Vxwv-,POqponl$Hjig%eB@@>}=<M:9wv6WsU2T|...- Whitespace - Code is written using only spaces, tabs, and newlines. Common byte values: “0x20” (Space), “0x09” (Tab), “0x0A” (Line Feed).
- PikaLang - Uses Pokémon-like sounds such as “pi”, “pika”, “ka”, “pipi”. Typically encodes data using custom encoding logic. May even implement RSA in challenges.
RSA Attacks and Variants
RSA attacks and variants refer to cryptanalysis techniques targeting weaknesses in RSA encryption. CTFs may present challenges involving classic RSA, multi-prime RSA, cube root attacks, Wiener’s attack, and more, requiring knowledge of number theory and cryptographic flaws.
- Classic RSA
- Given:
n: modulus (product of two primes)e: public exponentc: ciphertext
- Goal: Decrypt
cusing factorization ofn
- Given:
- Multi-Prime RSA
- Similar to classic RSA
nhas more than two prime factors- Makes
neasier to factor
- Cube Root Attack (Low Exponent Attack)
- Used when:
e = 3- Message
mis small
- Works if
m³ < n
- Used when:
- Wiener’s Attack
- Works when:
eis too larged(private exponent) is small
- Uses continued fractions to find
d
- Works when:
- Common Modulus Attack
- Given:
- Same
n - Different exponents
e1,e2 - Corresponding ciphertexts
c1,c2
- Same
- Works when plaintext is encrypted twice with different exponents
- Given:
- Chinese Remainder Theorem Attack
- Given:
p,q: prime factorsdp,dq: partial private keysc: ciphertext
- Reconstructs private key and decrypts
- Given:
- Twin Prime RSA
- Given:
n1,n2: moduli generated from twin primese: exponentc: ciphertext
- Exploits close relationship between
n1andn2to factor easily
- Given:
Symbol Cipher
Symbol ciphers use unique symbols or pictograms to represent letters or words. Examples include Pigpen, Futurama, Hylian, Dagger, Gravity Falls, and Dancing Men ciphers. Decoding these often requires reference charts or online tools.
- Pigpen Cipher A substitution cipher where letters are replaced with symbols based on a grid or “pigpen” shapes. Commonly seen in treasure hunts and historical codes.
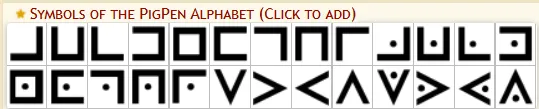
- Futurama Cipher Appeared in the animated series Futurama, this cipher uses alien-like symbols. Two versions exist as easter eggs within the show.

- Hylian Cipher (Twilight Princess)
A symbolic script from The Legend of Zelda: Twilight Princess. Mostly decorative but can be decoded to reveal messages..Cm7Xf-mw_223HkC.webp)
- Hylian Cipher (Skyward Sword)
Another Hylian variant from Skyward Sword, maps symbols directly to English letters, used throughout the game world..NPyNOkMK_2syjKD.webp)
- Hylian Cipher (Breath of the Wild)
Unique to Breath of the Wild, this version is used on signs, tablets, and game items. It has an established decoding chart..B6hMEbdX_Z14SFpO.webp)
- Dagger Alphabet
A fantasy-themed symbolic script often found in games or fictional lore. It functions as a substitution cipher with symbols representing letters.
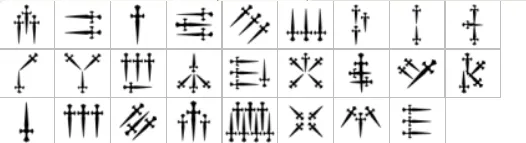
- Gravity Falls Cipher
- Used throughout the show Gravity Falls, these include Caesar, Atbash, A1Z26, and others. Fans decode hidden messages from end credits and clues.
 https://neerajlovecyber.com/decoders/gravity-falls-rune-cipher
https://neerajlovecyber.com/decoders/gravity-falls-rune-cipher
- Used throughout the show Gravity Falls, these include Caesar, Atbash, A1Z26, and others. Fans decode hidden messages from end credits and clues.
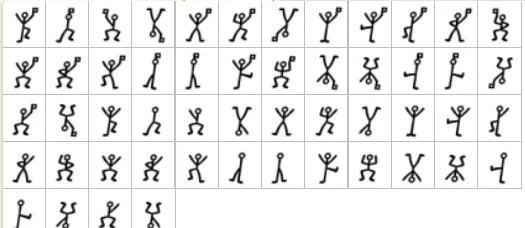
- Dancing Men Cipher
Inspired by Sherlock Holmes, this cipher uses stick figures in various poses to represent letters. It’s a monoalphabetic substitution cipher from the story The Adventure of the Dancing Men.
- Wingdings Font Cipher
The Wingdings Font Cipher is a substitution cipher that uses symbols from the Wingdings font to represent letters, numbers, and special characters.

- Standard Galactic Alphabet
The Standard Galactic Alphabet (SGA) is a fictional writing system from the popular game Minecraft. It’s a simple substitution cipher where each English letter is replaced by a unique symbol
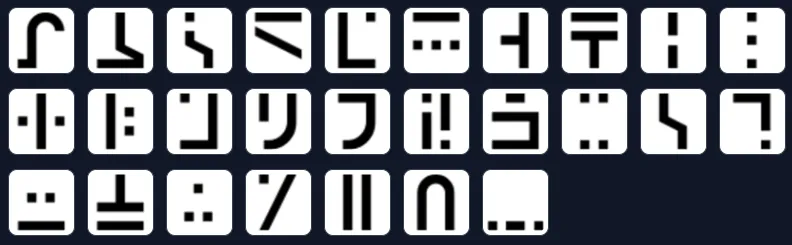 Decoder - https://neerajlovecyber.com/decoders/standard-galactic-alphabet
Decoder - https://neerajlovecyber.com/decoders/standard-galactic-alphabet - Bill Cipher (Gravity Falls) Popularized by the animated series Gravity Falls, this cipher has found its way into many CTF challenges, especially those with pop culture themes.
- Birds on a Wire Cipher A unique cipher that uses the position of birds on telephone wires to encode messages.
- Enderwalk Language Cipher A unique symbolic language from the game Minecraft, often used in puzzles and hidden messages.
- Gravity Falls Color Code Cipher A substitution cipher from Gravity Falls that uses colors to represent letters or numbers.
- Hexahue Alphabet A colorful cipher system that uses different colored hexagons to represent letters.
- Tic-Tac-Toe Cipher A simple substitution cipher where letters are mapped to positions on a tic-tac-toe grid.
- Unown Pokemon Alphabet Cipher A cipher based on the Unown Pokémon, where each Unown represents a letter of the alphabet.
Tools used for solving Crypto challenges
- Base65536 - Unicode’s answer to Base64.
- Braille Translator - Translate from braille to text.
- Ciphey - Tool to automatically decrypt encryptions without knowing the key or cipher, decode encodings, and crack hashes.
- CyberChef - A web app for encryption, encoding, compression and data analysis.
- Cryptii - Modular conversion, encoding and encryption online.
- dCode.fr - Solvers for Crypto, Maths and Encodings online.
- Decodify - Detect and decode encoded strings, recursively.
- Enigma Machine - Universal Enigma Machine Simulator.
- FeatherDuster - An automated, modular cryptanalysis tool.
- Galois - A fast galois field arithmetic library/toolkit.
- HashExtender - Tool for performing hash length extension attacks.
- Hash-identifier - Simple hash algorithm identifier.
- padding-oracle-attacker - CLI tool and library to execute padding oracle attacks easily.
- PadBuster - Automated script for performing Padding Oracle attacks.
- PEMCrack - Cracks SSL PEM files that hold encrypted private keys. Brute forces or dictionary cracks.
- PKCrack - PkZip encryption cracker.
- Polybius Square Cipher - Table that allows someone to translate letters into numbers.
- Quipqiup - Automated cryptogram solver.
- RsaCtfTool - RSA multi attacks tool.
- RSATool - Tool to to calculate RSA and RSA-CRT parameter.
- Rumkin Cipher Tools - Collection of ciphhers/encoders tools.
- Vigenere Solver - Online tool that breaks Vigenère ciphers without knowing the key.
- XOR Cracker - Online XOR decryption tool able to guess the key length and the cipher key to decrypt any file.
- XORTool - A tool to analyze multi-byte xor cipher.
- yagu - Automated integer factorization.
- Crackstation - Hash cracker (database).
- Online Encyclopedia of Integer Sequences - OEIS: The On-Line Encyclopedia of Integer Sequences
Frequently Asked Questions (FAQs) about CTF Cryptography
Q1: What’s the best way to start learning crypto for CTFs? A1: Begin with the basics! Understand common encoding schemes like Base64 and Hex, then move on to classical ciphers like Caesar and Vigenère. Practice solving simple challenges on platforms like PicoCTF or OverTheWire. Online resources like Cryptohack.org are also fantastic for hands-on learning.
Q2: What tools are essential for CTF crypto challenges? A2: You’ll definitely want a good online decoder/encoder like CyberChef (the “Swiss Army knife” of crypto). For more specific tasks, tools like dCode.fr, Ciphey (for automated decryption), and RsaCtfTool (for RSA attacks) are very useful. Don’t forget basic scripting languages like Python for custom solutions!
Q3: How do I identify the type of cipher in a CTF challenge? A3: Look for patterns!
- BaseXX encodings often have specific character sets and padding (
=). - ROT ciphers usually produce readable but shifted text.
- Classical ciphers might show frequency analysis patterns.
- Modern crypto usually involves large numbers (RSA) or specific file formats.
- The challenge description or file name often provides hints! Q4: What if I’m stuck on a crypto challenge? A4: Don’t give up!
- Re-read the prompt: Are there any hidden clues or hints you missed?
- Examine the input: Is it a common encoding? Does it look like a specific cipher output?
- Try different tools: If one tool doesn’t work, another might.
- Look for common attacks: If it’s RSA, think about low exponent, common modulus, or Wiener’s attack.
- Search online: Use keywords from the challenge and the ciphertext.
- Ask for hints (if allowed): In team CTFs, collaborate with teammates.
- Take a break: Sometimes stepping away and coming back with fresh eyes helps! Q5: Are there any common pitfalls in CTF crypto? A5: Yes!
- Not checking all encodings: A flag might be double or triple encoded.
- Ignoring context: The challenge description or accompanying files often hold crucial information.
- Overcomplicating simple ciphers: Sometimes, the simplest solution is the correct one.
- Not validating assumptions: Always verify your decryption or decoding steps.
- Case sensitivity: Some ciphers or tools are case-sensitive.
News Feed
Get the Hottest Cybersecurity News Delivered to You!
Thank you!
You have successfully joined our subscriber list.





