· Penetration Testing · 3 min read
SMTP Enumeration and Pentesting Guide for Email Server Security
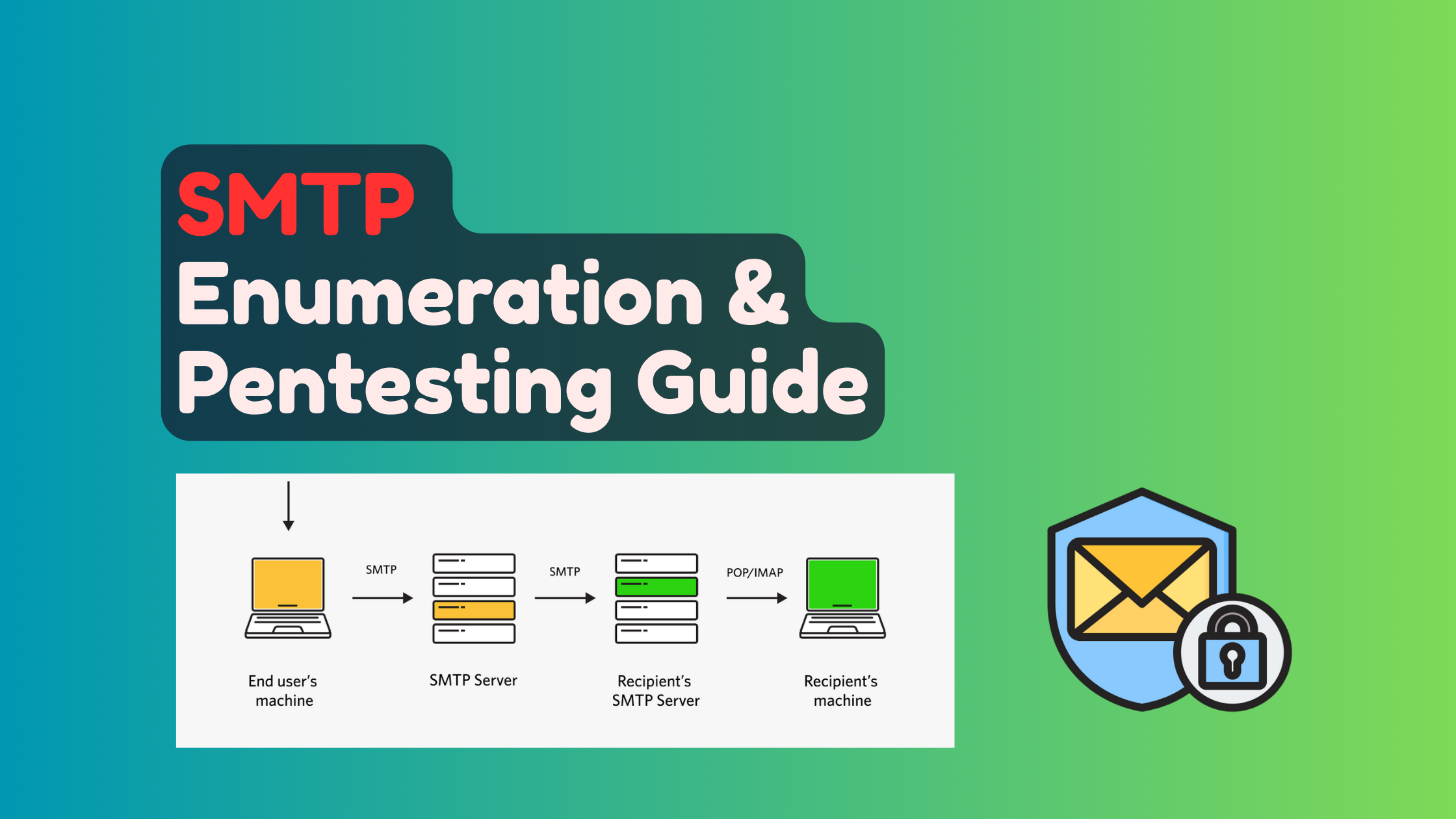
Table of Contents
43- 1.Understanding SMTP Architecture
- Key Components:
- 2.Common SMTP Vulnerabilities
- 1. Open Relays
- 2. Information Disclosure
- 3. Authentication Weaknesses
- 4. User Enumeration
- 3.Banner Grabbing Techniques
- Method 1: Using Telnet
- Method 2: Using Netcat
- Method 3: Using Nmap
- 4.User Enumeration Methods
- VRFY Command
- EXPN Command
- Automated Enumeration Tools
- Metasploit SMTP Enumeration
- Nmap SMTP Enumeration Script
- SMTP User Enum Tool
- 5.Advanced Enumeration Techniques
- Timing-Based Enumeration
- Response Code Analysis
- 6.SMTP Relay Attack Testing
- Detecting Open Relays
- Risks of Open Relays:
- 7.Brute Force Attack Testing
- Using Hydra
- Using Medusa
- Metasploit Brute Force Module
- 8.Securing SMTP Servers
- Essential Security Measures
- Advanced Security Configurations
- SPF Record Implementation
- DKIM Configuration
- DMARC Policy
- 9.Practical Testing Lab Setup
- Using Metasploitable 2 VM
- Banner Grabbing
- User Enumeration
- 10.Mitigation Strategies
- Immediate Actions:
- Long-term Security:
- 11.Best Practices for Penetration Testers
- 12.Conclusion
Email remains one of the most critical communication channels in modern organizations, making Simple Mail Transfer Protocol (SMTP) servers prime targets for cybercriminals. This comprehensive guide explores SMTP penetration testing methodologies, helping security professionals identify vulnerabilities before malicious actors can exploit them.
Understanding SMTP Architecture
SMTP operates as an application-layer protocol that facilitates email transmission between mail servers. The protocol typically uses port 25 for standard communication, port 465 for SMTP over SSL, and port 587 for secure authenticated transmission.
Key Components:
- Mail Transfer Agent (MTA): Transfers email between servers
- Mail Delivery Agent (MDA): Delivers email to recipient mailboxes
- Mail User Agent (MUA): End-user email client software
Common SMTP Vulnerabilities
1. Open Relays
Misconfigured SMTP servers that allow unauthorized email transmission can be exploited for spam distribution and phishing campaigns.
2. Information Disclosure
Verbose banners often reveal server software versions, making vulnerability identification easier for attackers.
3. Authentication Weaknesses
Servers lacking proper authentication mechanisms or using weak credentials become easy targets for unauthorized access.
4. User Enumeration
Improperly configured servers may allow attackers to verify email addresses using VRFY and EXPN commands.
Banner Grabbing Techniques
Banner grabbing reveals crucial information about target SMTP servers, including software versions and configurations.
Method 1: Using Telnet
telnet target_ip 25Method 2: Using Netcat
nc target_ip 25Method 3: Using Nmap
nmap -sV -p 25 target_ipUser Enumeration Methods
VRFY Command
The VRFY command verifies if specific users exist on the server:
VRFY admin@example.comEXPN Command
The EXPN command reveals mailing list members:
EXPN staff@example.comAutomated Enumeration Tools
Metasploit SMTP Enumeration
use auxiliary/scanner/smtp/smtp_enumset RHOSTS target_ipset USER_FILE /path/to/usernames.txtrunNmap SMTP Enumeration Script
nmap --script smtp-enum-users -p 25 target_ipSMTP User Enum Tool
smtp-user-enum -M VRFY -U /path/to/userlist.txt -t target_ipAdvanced Enumeration Techniques
Timing-Based Enumeration
Attackers measure server response times to differentiate between valid and invalid users:
- Valid users: Slower response (150ms)
- Invalid users: Faster response (100ms)
Response Code Analysis
Different SMTP response codes can indicate user validity:
- 250 OK: Valid user
- 550 No such user: Invalid user
SMTP Relay Attack Testing
Detecting Open Relays
nmap -p 25 --script smtp-open-relay target_ipRisks of Open Relays:
- Spam propagation
- IP blacklisting
- Phishing and malware distribution
Brute Force Attack Testing
Using Hydra
hydra -l user -P /path/to/passwords.txt smtp://target_ip -VUsing Medusa
medusa -h target_ip -u user -P /path/to/passwords.txt -M smtpMetasploit Brute Force Module
use auxiliary/scanner/smtp/smtp_loginset RHOSTS target_ipset USER_FILE /path/to/usernames.txtset PASS_FILE /path/to/passwords.txtrunSecuring SMTP Servers
Essential Security Measures
- Disable Open Relay: Require authentication for email transmission
- Remove Verbose Banners: Limit information disclosure
- Implement Strong Authentication: Use SASL mechanisms
- Enable TLS Encryption: Protect data in transit
- Disable VRFY/EXPN: Prevent user enumeration
Advanced Security Configurations
SPF Record Implementation
example.com. IN TXT "v=spf1 mx ip4:192.168.1.100 -all"DKIM Configuration
DKIM-Signature: v=1; a=rsa-sha256; d=example.com; s=key;DMARC Policy
_dmarc.example.com. IN TXT "v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com"Practical Testing Lab Setup
Using Metasploitable 2 VM
Banner Grabbing
telnet 192.168.1.61 25netcat 192.168.1.61 25nmap -sV -p 25 192.168.1.61User Enumeration
# Telnet methodtelnet 192.168.1.61 25VRFY msfadmin# Metasploit methodmsfconsolesearch smtp useruse auxiliary/scanner/smtp/smtp_enumset RHOST 192.168.1.61exploitMitigation Strategies
Immediate Actions:
- Disable unnecessary SMTP commands
- Implement proper authentication
- Configure TLS encryption
- Set up monitoring and logging
Long-term Security:
- Regular vulnerability assessments
- Security patch management
- Employee security training
- Incident response planning
Best Practices for Penetration Testers
- Always obtain proper authorization before testing
- Document all findings thoroughly
- Provide clear remediation steps
- Test in isolated environments when possible
- Follow responsible disclosure practices
Conclusion
SMTP penetration testing is crucial for maintaining email security in modern organizations. By understanding common vulnerabilities and implementing proper testing methodologies, security professionals can identify and address weaknesses before they become security incidents. Regular testing, combined with proper security configurations, helps ensure robust email infrastructure protection. Remember that penetration testing should always be conducted with proper authorization and within legal boundaries. The techniques outlined in this guide should be used responsibly for defensive purposes only.
Stay updated with the latest cybersecurity trends and penetration testing techniques by following our blog and joining our community of security professionals.
News Feed
Get the Hottest Cybersecurity News Delivered to You!
Thank you!
You have successfully joined our subscriber list.