· Steganography · 4 min read
Steganography Cheatsheet for CTF Beginners

Table of Contents
25- 1.Step-by-Step File Analysis
- Basic Commands
- Metadata Extraction
- 2.Embedded File Discovery
- Binwalk – File Carving Tool
- Example: Extracting Hidden Files from an Image
- 3.Image Steganography
- Visual Tricks
- Bit-Level Tools
- Extraction Tools
- Online Tools
- 4.Audio Steganography
- Useful Tools
- 5.Video Steganography
- Frame & Audio Extraction
- 6.PDF Stego
- Text & Metadata
- Crack Protected PDFs
- 7.Network-Based Challenges
- Wireshark
- 8.Advanced Tricks & Scripts
- Convert Binary to Image
- Invert Pixel Colors (Python)
- 9.OSINT & Comparisons
- 10.Tool Index (Summary)
Steganography is the art of concealing messages in plain sight — hiding data in files that appear normal. In Capture The Flag (CTF) contests, stego challenges often hide flags inside images, audio, videos, PDFs, or metadata.
Step-by-Step File Analysis
Basic Commands
file target.jpg strings target.jpg | head -n 50 xxd target.jpg | head hexdump -C target.jpg | headCheck the file’s true type, readable strings, and hex patterns. You may discover plaintext flags, passwords, or data headers.
Metadata Extraction
exiftool target.jpgExtract EXIF comments, timestamps, GPS info, and hidden metadata.
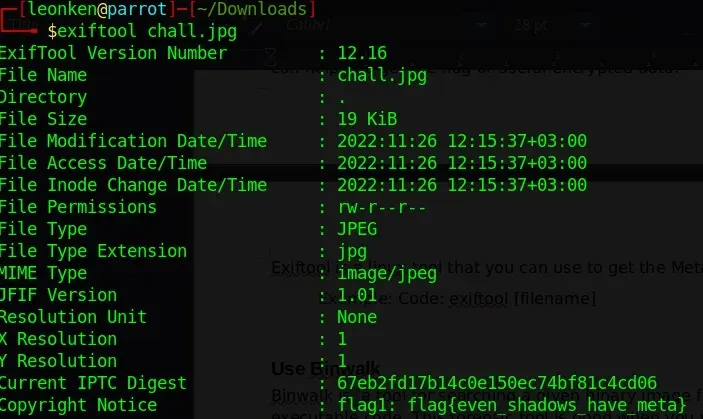 Also try:
Also try:
exiv2 target.jpgFor direct metadata manipulation or cleanup.
Embedded File Discovery
Binwalk – File Carving Tool
binwalk -Me target.jpg
Key Options:
-e: Extract embedded files-M: Recursive extraction-z: Carve data blocks without extraction-R: Raw hex pattern match (e.g.,\x1f\x8bfor gzip)-E: Entropy scanning-W: Hex diff mode Useddif you manually need to extract embedded segments.
Example: Extracting Hidden Files from an Image
Let’s walk through a practical use case with a stego challenge:
Step 1:
Start with a quick string check:
strings PurpleThing.jpeg | grep {No flag found via visible strings.
Step 2:
Now inspect with binwalk:
binwalk PurpleThing.jpegOutput:
DECIMAL HEXADECIMAL DESCRIPTION ---------------------------------------------------------------------------- 0 0x0 PNG image, 780 x 720, 8-bit/color RGBA, non-interlaced 41 0x29 Zlib compressed data, best compression 153493 0x25795 PNG image, 802 x 118, 8-bit/color RGBA, non-interlacedWe clearly see embedded PNG and Zlib data.
Step 3:
Extract the hidden files using:
binwalk -D 'image:png' PurpleThing.jpegThis creates a folder named _PurpleThing.jpeg.extracted/, containing extracted files like 25795.png.
Step 4:
Open that file and boom — the flag is there:
ABCTF{b1nw4lk_is_us3ful}Image Steganography
Visual Tricks
- Open image and observe — flag may be painted in.
- Use GIMP: adjust brightness, contrast, curves, color levels.
- Use ImageMagick to compare images:
compare original.png modified.png diff.pngBit-Level Tools
| Tool | Usage |
|---|---|
| stegsolve | Bit-plane viewer (bit-level hidden info) |
| zsteg | Bit analysis of PNG/BMP |
| stegonline | Web-based image steg operations |
| Steganabara | LSB amplifier & visualizer |
| sigBits | Significant bits stego decoder |
| pngcheck | Dump/analyze PNG chunks |
| pngtools | Deep chunk-level PNG analysis |
Stegsolve -
Use stegsolve to identify QR codes, LSB data, or color-filtered patterns.
A great GUI tool that covers a wide range of analysis, some of which is covered by the other tools mentioned above and a lot more including color profiles, planes, Color maps, strings.
Example Challange: Looks like a blank image
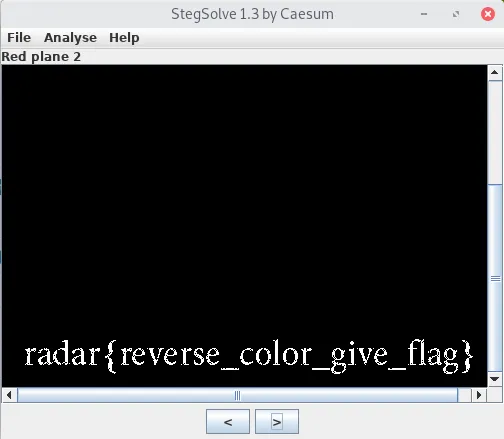
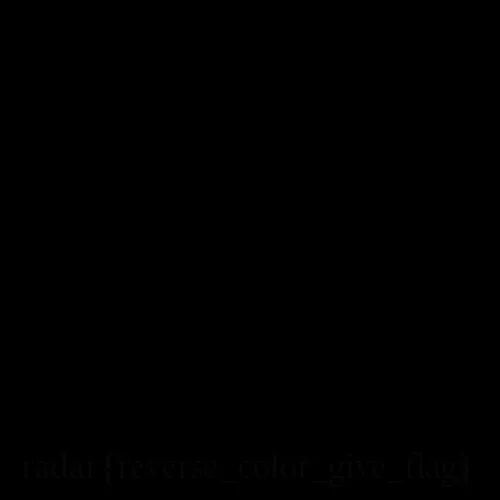 Solution: Opening the image in Stegsolve and clicking through the planes gives us a flag. Image below.
Solution: Opening the image in Stegsolve and clicking through the planes gives us a flag. Image below.
Extraction Tools
| Tool | Usage |
|---|---|
| steghide | Hide/extract in JPG, BMP, WAV |
| stegseek | Fast brute-force for steghide |
| stegcracker | Brute-force JPG stego files |
| outguess | Stego in JPG/PPM files |
| stegextract | Auto-detect hidden data |
| jsteg | LSB-based JPEG stego |
| stegpy | Simple Python LSB tool |
| stegosaurus | Embed data into Python bytecode |
| Snow/stegsnow | Whitespace stego tool |
Example:
steghide extract -sf secret.jpg stegseek secret.jpg rockyou.txtOnline Tools
- StegOnline
- Steganography Online
- Image Steganography
- FotoForensics
- AperiSolve – Multi-layer analyzer
- Image ELA – Error level analysis (detects manipulations)
Audio Steganography
Useful Tools
| Tool | Purpose |
|---|---|
| DeepSound | Hide/extract files in .wav audio |
| sonic-visualiser | Visualize spectrograms, waveforms |
| audacity | Waveform editing, reversal, decoding |
| Snow / stegsnow | Whitespace stego in audio |
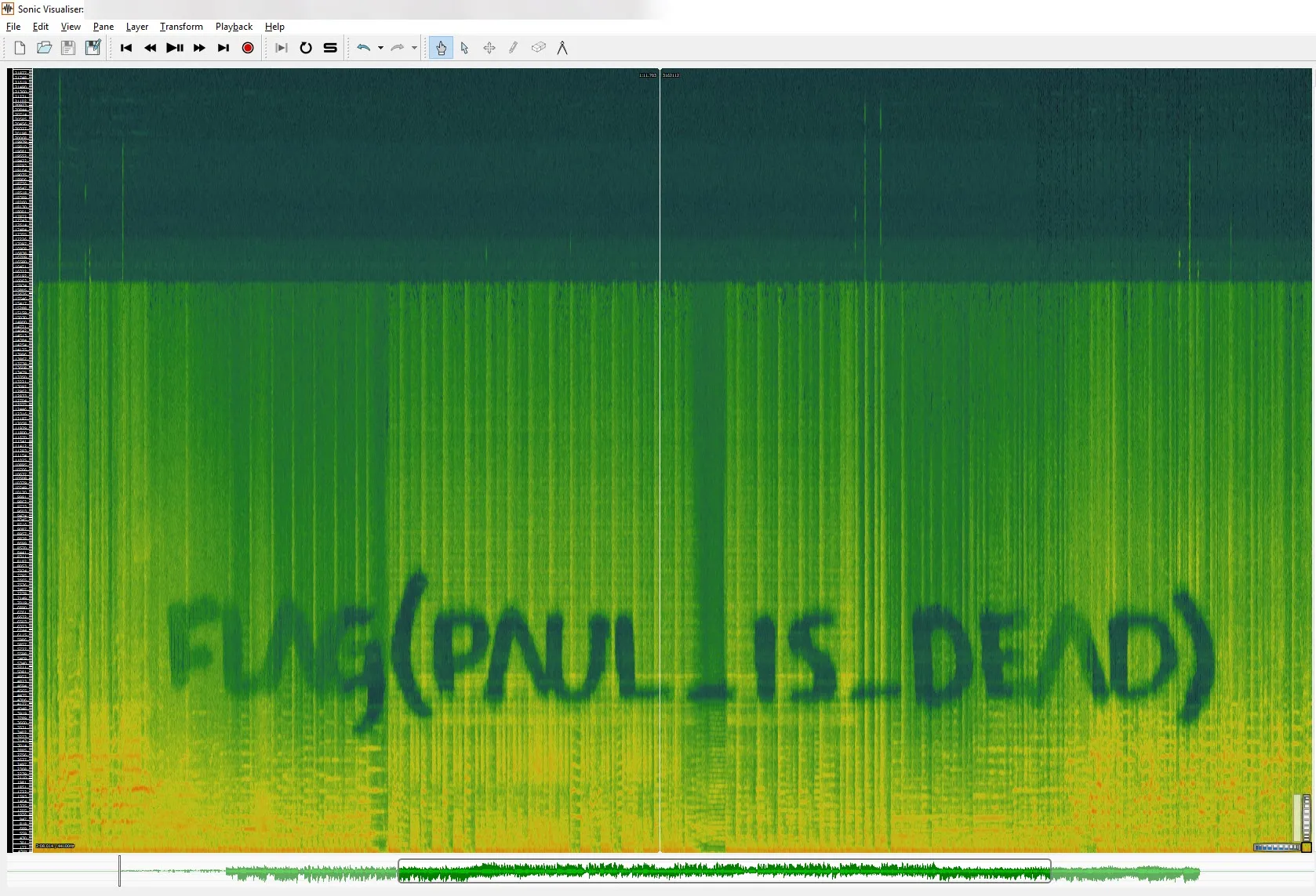
Use sonic-visualiser with linear/log scale spectrogram + contrast filters.
Sonic Visualizer is a great tool to find hidden messages in audio files.
Remember that just because it’s a mp3 does not mean it’s going to have an answer in the spectrogram. I am going to show you one more Spectrogram with a flag in it.
Video Steganography
Frame & Audio Extraction
ffmpeg -i video.mp4 frame_%04d.png- Analyze individual frames using
zsteg,stegsolve. - Open audio separately in Audacity for reverse/LSB tricks.
Tool:
hipshot — Convert video/photo series into long-exposure-style images to reveal stego data.
PDF Stego
Text & Metadata
pdfinfo file.pdf pdftotext file.pdf output.txtCrack Protected PDFs
pdf2john file.pdf > hash.txt john --wordlist=rockyou.txt hash.txtNetwork-Based Challenges
Wireshark
Sometimes you’ll get .pcap files. Open them in Wireshark and follow the TCP or HTTP stream to uncover credentials or base64-encoded data.
- Right-click a packet → Follow → TCP Stream
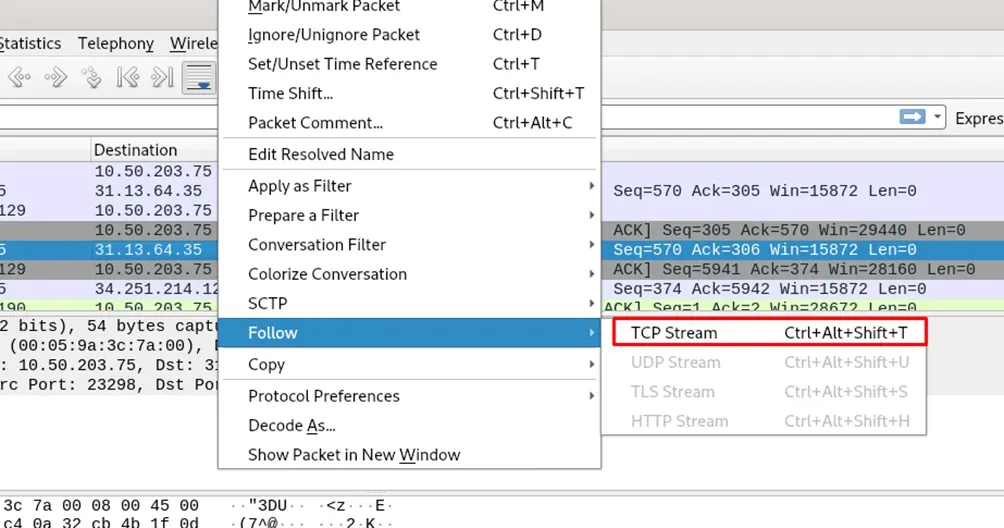 Look for anything readable—sometimes even the flag itself!
Look for anything readable—sometimes even the flag itself!
Advanced Tricks & Scripts
Convert Binary to Image
convert -depth 8 -size 300x300+0 gray:data.raw output.pngView strange binary blobs visually.
Invert Pixel Colors (Python)
import Imageif __name__ == '__main__': img = Image.open('input.png') in_pixels = list(img.getdata()) out_pixels = list() for i in range(len(in_pixels)): r = in_pixels[i][0] g = in_pixels[i][1] b = in_pixels[i][2] out_pixels.append( (255-r, 255-g, 255-b) ) out_img = Image.new(img.mode, img.size) out_img.putdata(out_pixels) out_img.save("output_inverted.png", "PNG")the image looks like it’s just a random noise we should make sure of it. We can, in fact, measure its randomness. Pixels of each color can appear in each place of the image with equal chance. If it’s false for some colors, we certainly want to look at them. Here is a script for that, and the results appears below:
$ php solve.php image.pngMAX disp: 1492.41; AVG: 92.82GAP: 351.61 ± 200DONE.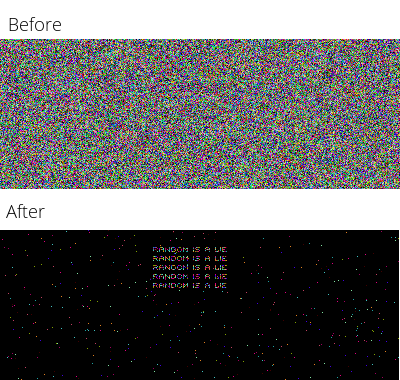
OSINT & Comparisons
- TinEye: Reverse search
- Use ImageMagick or diff-pixel tools for overlays
- Compare layers in Adobe/GIMP if image has metadata for layer stacking
Tool Index (Summary)
| Tool | Category | Function |
|---|---|---|
| AperiSolve | Online | Layer inspection |
| FotoForensics | Online | ELA and manipulation detection |
| BPStegano | CLI | LSB encoding (Python3) |
| Stegsolve | GUI (Java) | Bit-layer viewer |
| Zsteg | CLI | PNG/BMP LSB decoding |
| Steghide | CLI | Stego in image/audio |
| Stegseek | CLI | Brute-force steghide |
| Outguess | CLI | JPG/PPM stego |
| Snow / Stegsnow | CLI | Whitespace stego |
| jsteg | CLI | JPEG LSB |
| sigBits | CLI | LSB decoder |
| stegcracker | CLI | JPG bruteforce stego |
| stegextract | CLI | Auto extract data |
| ImageMagick | CLI | Compare, convert, XOR |
| pngcheck | CLI | PNG chunk inspection |
| pngtools | CLI | Advanced PNG analysis |
| StegOnline | Web | Encode/Decode images |
| Image Steganography | Web | JS-based LSB tool |
| OpenStego | GUI | Random LSB |
| DeepSound | GUI | Audio file steganography |
| hipshot | CLI | Video → long exposure frame |
| sonic-visualiser | GUI | Audio spectrum viewer |
| DTMF Tools | Audio | Decode dial tones |
| pdf2john | CLI | Crack PDF password |
| Stegosaurus | Python | Embed in bytecode |
| StegoVeritas | Python | Multi-stego toolkit |
| Stegpy | Python | Basic LSB tool |
| BPStegano | Python | LSB encoding (Python3) |
| Steganabara | GUI | LSB amplifier & visualizer |
| Magic Eye Solver | Web | Hidden info from images |
| SmartDeblur | GUI | Deblur images |
| Exiv2 | CLI | Image metadata manipulation |
| Exif | CLI | Show EXIF info |
| Stegbreak | CLI | Brute-force JPG stego |
| Binwalk | CLI | Embedded file extraction |
News Feed
Get the Hottest Cybersecurity News Delivered to You!
Thank you!
You have successfully joined our subscriber list.





