· Neeraj Singh · Security · 8 min read
Symbol Ciphers in CTF Challenges: A Complete Guide to Decoding Visual Cryptography

Table of Contents
38- 1.What Are Symbol Ciphers?
- Why Symbol Ciphers Are Popular in CTFs
- 2.Common Symbol Ciphers in CTF Challenges
- 1. Pigpen Cipher (Masonic Cipher)
- 2. Wingdings Font Cipher
- 3. Dancing Men Cipher
- 4. Bill Cipher (Gravity Falls)
- 5. Dagger Alphabet Cipher
- 6. Standard Galactic Alphabet
- 7. Gravity Falls Rune Cipher
- 8. Birds on a Wire Cipher
- 9. Hexahue Alphabet
- 10. Enderwalk Language Cipher
- 11. Gravity Falls Color Code Cipher
- 12. Tic-Tac-Toe Cipher
- 13. Unown Pokemon Alphabet Cipher
- 14. Futurama Cipher
- 15. Hylian Cipher (Twilight Princess)
- 16. Hylian Cipher (Skyward Sword)
- 17. Hylian Cipher (Breath of the Wild)
- 3.Methodology for Solving Symbol Ciphers
- Step 1: Initial Analysis
- Step 2: Cipher Identification
- Step 3: Decoding Process
- Step 4: Verification and Refinement
- Step 5: Advanced Techniques
- 4.Frequently Asked Questions (FAQs)
- Q: How do I know which symbol cipher I’m dealing with?
- Q: What if the symbols don’t match any known cipher exactly?
- Q: How important is frequency analysis for symbol ciphers?
- Q: Should I try automated tools or decode manually?
- Q: What if there are multiple symbol sets in one challenge?
- Q: How do I handle symbols that look very similar?
- Q: What’s the best way to practice symbol cipher recognition?
- Q: Are there any common mistakes to avoid?
- Q: What tools should I have ready for symbol cipher challenges?
- Q: How do I approach team-based symbol cipher challenges?
- 5.Conclusion
Symbol ciphers are among the most visually striking and intellectually engaging challenges you’ll encounter in CTF (Capture The Flag) competitions. Unlike traditional text-based cryptography, these ciphers replace letters with unique symbols, creating mysterious messages that require both pattern recognition and cryptographic knowledge to decode.
In this comprehensive guide, we’ll explore the most common symbol ciphers found in CTF challenges, provide practical decoding techniques, and give you hands-on tools to master these visual puzzles.
What Are Symbol Ciphers?
Symbol ciphers are substitution ciphers that replace each letter of the alphabet with a unique symbol, geometric shape, or pictograph. They’ve been used throughout history by secret societies, military organizations, and cryptographers to conceal messages in plain sight.
Why Symbol Ciphers Are Popular in CTFs
- Visual Appeal: They create intriguing puzzles that immediately catch participants’ attention
- Historical Significance: Many have fascinating backstories that add educational value
- Pattern Recognition: They test both cryptographic and visual analysis skills
- Scalable Difficulty: Can range from simple substitution to complex multi-layered challenges
Common Symbol Ciphers in CTF Challenges
1. Pigpen Cipher (Masonic Cipher)
The Pigpen cipher is arguably the most frequently encountered symbol cipher in CTF competitions. Used historically by Freemasons, it replaces letters with symbols derived from a grid pattern.
Recognition Patterns:
- Symbols made of lines, angles, and dots
- Grid-like or fence-like appearance
- Often includes triangular shapes
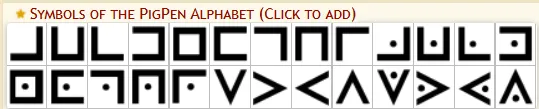
Pigpen Cipher Encoder/Decoder
Encode and decode messages using the Pigpen cipher, a simple substitution cipher that uses symbols t...
CTF Tips for Pigpen:
- Look for repeated patterns that might indicate common letters (E, T, A)
- Count symbol frequency to identify potential vowels
- Check if the cipher uses dots to distinguish similar symbols
2. Wingdings Font Cipher
Microsoft’s Wingdings font has become a popular choice for CTF creators due to its accessibility and variety of symbols.
Recognition Patterns:
- Mix of arrows, hands, faces, and geometric shapes
- Symbols that look like they could be from a computer font
- Often includes recognizable icons

Wingdings Font Cipher Encoder/Decoder
Encode and decode messages using the Wingdings Font Cipher, a substitution cipher that uses Wingding...
CTF Strategies:
- Try copying suspicious symbols into a text editor and changing the font to Wingdings
- Look for patterns in symbol complexity or style
- Consider that some CTF creators use Wingdings 2 or 3 variants
3. Dancing Men Cipher
Inspired by Arthur Conan Doyle’s Sherlock Holmes story, this cipher uses stick figures in various poses to represent letters.
Recognition Patterns:
- Stick figure drawings in different positions
- Some figures may hold flags or have raised arms
- Usually drawn in a linear sequence
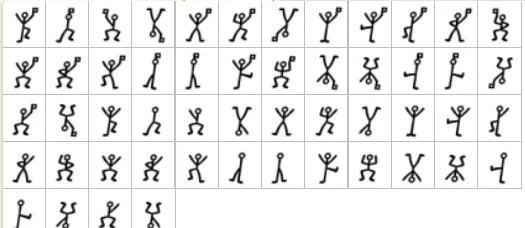
Dancing Men Cipher Encoder/Decoder
Encode and decode messages using the Dancing Men Cipher, a substitution cipher from the Sherlock Hol...
Decoding Approach:
- Flags or special poses often indicate word endings
- Frequency analysis works well with longer messages
- Look for single-character “words” that likely represent ‘A’ or ‘I’
4. Bill Cipher (Gravity Falls)
Popularized by the animated series Gravity Falls, this cipher has found its way into many CTF challenges, especially those with pop culture themes.
Recognition Patterns:
- Triangular and angular symbols
- Often includes eye-like symbols
- May have a mystical or occult appearance
Bill Cipher Encoder/Decoder
Encode and decode messages using the Bill Cipher, a substitution cipher from the show Gravity Falls.
5. Dagger Alphabet Cipher
A fantasy-themed symbolic script often found in games or fictional lore. Functions as a substitution cipher with symbols representing letters.
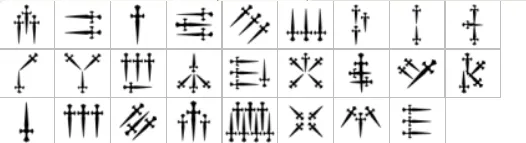
Daggers Alphabet Cipher Encoder/Decoder
Encode and decode messages using the Daggers Alphabet cipher, a substitution cipher that uses dagger...
6. Standard Galactic Alphabet
The Standard Galactic Alphabet (SGA) is a fictional writing system from Minecraft. It’s a simple substitution cipher where each English letter is replaced by a unique symbol.
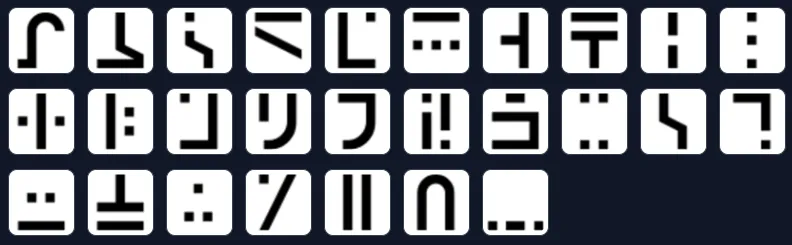
Standard Galactic Alphabet Encoder/Decoder
Encode and decode messages using the Standard Galactic Alphabet, a fictional writing system from Min...
7. Gravity Falls Rune Cipher
Used throughout the show Gravity Falls, these include Caesar, Atbash, A1Z26, and others. Fans decode hidden messages from end credits and clues.

Gravity Falls Rune Cipher Encoder/Decoder
.Dfm60E2r.png) A
A .Q_Nwti9R.png) B
B .upguMUvl.png) C
C .BexO33G7.png) D
D .DzrEe4we.png) E
E Encode and decode messages using the Gravity Falls Rune Cipher, a mystical substitution cipher from ...
8. Birds on a Wire Cipher
A unique cipher that uses the position of birds on telephone wires to encode messages.
Birds on a Wire Cipher Encoder/Decoder
 A
A  B
B  C
C  D
D  E
E Encode and decode messages using the Birds on a Wire Cipher, a substitution cipher where letters are...
9. Hexahue Alphabet
A colorful cipher system that uses different colored hexagons to represent letters.
Hexahue Alphabet Cipher Encoder/Decoder
Encode and decode messages using the Hexahue Alphabet Cipher, a substitution cipher where letters ar...
10. Enderwalk Language Cipher
A unique symbolic language from the game Minecraft, often used in puzzles and hidden messages.
Enderwalk Language Encoder/Decoder
._7KfTqUD.png) A
A .BGfvr60d.png) B
B .UdUBr1Ic.png) C
C .C94ioTvS.png) D
D .CHxRUgE9.png) E
E Encode and decode messages using the Enderwalk Language cipher, a mysterious alien-like script inspi...
11. Gravity Falls Color Code Cipher
A substitution cipher from Gravity Falls that uses colors to represent letters or numbers.
Gravity Falls Color Code Encoder/Decoder
Encode and decode messages using the Gravity Falls Color Code cipher, a vibrant substitution cipher ...
12. Tic-Tac-Toe Cipher
A simple substitution cipher where letters are mapped to positions on a tic-tac-toe grid.
Tic-Tac-Toe Cipher Encoder/Decoder
Encode and decode messages using the Tic-Tac-Toe cipher, a grid-based substitution cipher that uses ...
13. Unown Pokemon Alphabet Cipher
A cipher based on the Unown Pokémon, where each Unown represents a letter of the alphabet.
Unown Pokemon Alphabet Encoder/Decoder
.ZrprDxl1.png) A
A .DW9XAGPM.png) B
B .CSIfEL_Q.png) C
C .DVh3OoMW.png) D
D .DnfyKv7i.png) E
E Encode and decode messages using the Unown Pokemon Alphabet cipher, featuring the mysterious letter-...
14. Futurama Cipher
Appeared in the animated series Futurama, this cipher uses alien-like symbols. Two versions exist as easter eggs within the show.
15. Hylian Cipher (Twilight Princess)
A symbolic script from The Legend of Zelda: Twilight Princess. Mostly decorative but can be decoded to reveal messages.
16. Hylian Cipher (Skyward Sword)
Another Hylian variant from Skyward Sword, maps symbols directly to English letters, used throughout the game world.
17. Hylian Cipher (Breath of the Wild)
Unique to Breath of the Wild, this version is used on signs, tablets, and game items. It has an established decoding chart.
Methodology for Solving Symbol Ciphers
When encountering a symbol cipher in a CTF challenge, follow this systematic approach to maximize your chances of success:
Step 1: Initial Analysis
- Document the symbols: Take screenshots or carefully copy all unique symbols
- Count symbol frequency: Identify which symbols appear most often
- Look for patterns: Notice repeated sequences, spacing, or groupings
- Identify context clues: Check challenge descriptions, titles, or hints for cipher type indicators
Step 2: Cipher Identification
- Visual comparison: Compare symbols against known cipher alphabets
- Historical context: Consider the challenge theme (medieval, sci-fi, gaming, etc.)
- Symbol characteristics: Analyze if symbols are geometric, pictographic, or abstract
- Reference databases: Use online cipher identification tools and databases
Step 3: Decoding Process
- Start with frequency analysis: Map most common symbols to common English letters (E, T, A, O, I, N)
- Look for single-letter words: These are likely ‘A’ or ‘I’
- Identify short words: Two-letter words like ‘TO’, ‘OF’, ‘IN’ can provide breakthrough clues
- Use partial solutions: Fill in known letters and look for recognizable word patterns
- Apply linguistic knowledge: Consider common letter combinations and word structures
Step 4: Verification and Refinement
- Check for meaningful text: Ensure decoded message makes sense in context
- Validate against challenge requirements: Confirm the solution format matches expected output
- Look for flag format: Most CTF flags follow patterns like
CTF{decoded_message}orflag{answer}
Step 5: Advanced Techniques
- Consider cipher variants: Some challenges use modified or layered cipher systems
- Check for steganography: Symbols might hide additional information in color, size, or position
- Apply multiple decoding steps: The symbol cipher might be one layer of a multi-stage puzzle
Frequently Asked Questions (FAQs)
Q: How do I know which symbol cipher I’m dealing with?
A: Start by analyzing the visual characteristics of the symbols. Geometric shapes with lines and dots often indicate Pigpen cipher, while stick figures suggest Dancing Men. Computer-style icons might be Wingdings, and triangular mystical symbols could be Bill Cipher. When in doubt, try the most common ones first: Pigpen, Wingdings, and Dancing Men.
Q: What if the symbols don’t match any known cipher exactly?
A: Many CTF challenges use custom or modified symbol ciphers. In these cases, treat it as a standard substitution cipher and use frequency analysis. Look for patterns in symbol complexity or visual similarity that might group related letters (like vowels or consonants).
Q: How important is frequency analysis for symbol ciphers?
A: Frequency analysis is crucial, especially for longer messages. In English, ‘E’ appears about 12% of the time, followed by ‘T’ (9%) and ‘A’ (8%). Map your most frequent symbols to these letters first, then work on common short words and letter combinations.
Q: Should I try automated tools or decode manually?
A: Start with manual analysis to understand the cipher structure, then use automated tools to speed up the process. Many online decoders can handle standard symbol ciphers, but custom CTF ciphers often require manual work or custom scripts.
Q: What if there are multiple symbol sets in one challenge?
A: Some challenges combine different cipher types or use symbols to represent different alphabets. Look for visual groupings, different symbol styles, or context clues that might indicate where one cipher ends and another begins.
Q: How do I handle symbols that look very similar?
A: Pay attention to small details like dot placement, line thickness, or orientation. In Pigpen cipher, for example, the presence or absence of dots is crucial. When in doubt, try both interpretations and see which produces more meaningful text.
Q: What’s the best way to practice symbol cipher recognition?
A: Use the interactive decoders provided in this guide, participate in practice CTFs, and study historical examples. Create your own messages using different symbol ciphers to understand how they work from the encoder’s perspective.
Q: Are there any common mistakes to avoid?
- Don’t assume the first cipher you try is correct; verify your solution makes sense
- Watch out for red herrings - not every symbol-like image is actually a cipher
- Remember that some challenges use cipher keys or offsets
- Don’t forget to check for standard CTF flag formats in your decoded text
Q: What tools should I have ready for symbol cipher challenges?
A: Keep bookmarks to online cipher databases (like dCode), have image editing software for symbol analysis, maintain a reference sheet of common cipher alphabets, and consider learning basic Python for custom decoding scripts.
Q: How do I approach team-based symbol cipher challenges?
A: Divide tasks: one person documents symbols, another performs frequency analysis, and a third researches cipher types. Share findings regularly and don’t hesitate to get fresh eyes on the problem if you’re stuck.
Conclusion
Symbol ciphers represent a fascinating intersection of visual art, historical knowledge, and cryptographic skill. Mastering these challenges requires patience, pattern recognition abilities, and a systematic approach to analysis.
Whether you’re encountering a classic Pigpen cipher or a custom symbol system designed specifically for a CTF, remember that the fundamental principles remain the same: observe patterns, analyze frequency, and apply logical deduction.
The interactive tools provided in this guide will help you practice and develop your skills. Start with the simpler ciphers like Pigpen, then gradually work your way up to more complex symbol systems.
Remember: The key to success in CTF symbol cipher challenges is practice, patience, and persistence. Each cipher you solve builds your pattern recognition skills and expands your cryptographic toolkit.
Happy decoding!
Want to practice more? Check out our interactive decoder tools for hands-on experience with various symbol ciphers.
Share this post
News Feed
Get the Hottest Cybersecurity News Delivered to You!
Thank you!
You have successfully joined our subscriber list.